By Melchior zum grauen Wolf, OP
(mka Kevin Baun)
Alberti cipher. (2024, January 9). In Wikipedia. https://en.wikipedia.org/wiki/Alberti_cipher
The Oxford dictionary defines the word cipher as “a secret or disguised way of writing”. A cipher is overt, it doesn’t try to hide that it is a cipher. The job of a cipher isn’t to disguise information as you would with a steganographici system but rather to keep information confidential. Perhaps the best way to understand what a cipher is to look at the origin of the word itself. The English word cipher is taken from the old French ‘cifre’, derived from the Latin ‘cifra’, which was in turn adopted from the Arabic word ‘صفر’ (sifr) meaning zero or null. Looking at this etymology we can glean a more contextual understanding of the word cipher as being a message that is unknowable. It is from this simple notion of mystery that we enter into the study of cryptology, the study of the science of secret writing which is known as cryptography.
The focus of this introduction to medieval cryptography is on cryptography of the occident. That being said, I would like to take a moment to discuss the origins of secret writing that would later develop into what we think of as cryptography. It is generally held that cryptography was derived from an Egyptian scribal practice that is shown to date back to at least 1900 BCE, or approximately the time of Khumhotep IIii. Several authors have described how scribes would use alternate dialects to draw attention to certain passages or even, as Bauer (2019) details, arrange pictograms in such a way that changing the order of interpterion alters the meaning of the message itself. This displayed a clandestine quality due to the fact that the reader needed to be knowledgeable of the dialects being used or the operations required to derive the obfuscated meaning. From here the art of secret writing moved north into the Arab world and eventually west into Europe with some of the earliest references there being seen in the Greek writings of Archilochus and Aneas Tacticus in the 7th and 4th centuries, respectively. These early western approaches to conveying secret messages primarily consisted of transposition devices such as the scytale and encoding devices such as the Aneas Disciii. While these approaches advanced the ways in which messages may be secured they remained more of an art than a science.
G. B. Porta’s description of the scytale, De occultis literarum notis libri IV (1593)
One of the earliest written schemes that we encounter in the western world is an encoding approach popularized by Polybius around 150 BCEiv. The ‘Polybius Square’, as it would come to be known, lays out the Grecian alphabet in a 5×5 grid of 24 characters (the last space being a null value). There are several methods of encoding that this grid can be used for. The primary method, as described by Polybius, was for a system of telegraphy. Below you can see the originally described grid of 24 characters and a 25 character Latin alphabet where the letters I and J are represented with an I.
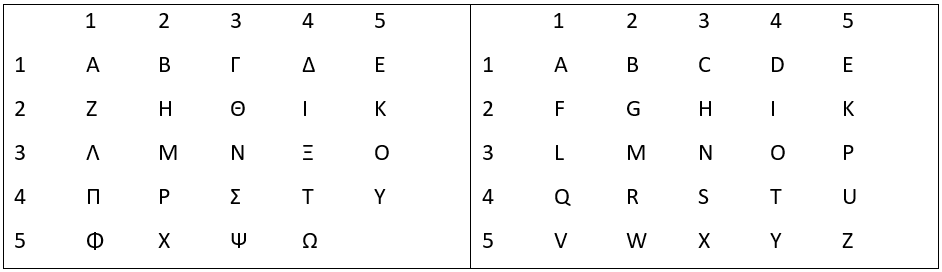
Polybius outlines a system whereby a message could be encoded using the grid such that each letter of the message is indicated by its coordinate index. Then the message sender would transmit by holding up the corresponding number of signal torches to be seen by the recipient from a distance. The coordinates are determined by finding each letter and combining the horizontal value (row) with the vertical value (column). Using this technique we would encode the word CAT as 13 11 44 since C occupies the first row, third column. A occupies the first row, first column. T occupies the fourth row, forth column. Using this example the sender would hold up 1 torch next to 3 torches, and so on, until the message has been completed. This takes us a step closer to a concept that would come to dominate western cryptography throughout the Middle Ages, the substitution cipherv.
A substitution cipher is exactly what it sounds like. One thing is substituted for another in order to make the resulting message immediately unreadable. Substitution ciphers come in several different flavors but they can generically be grouped into being either mono or poly alphabetic. As the name implies monoalphabetic ciphers substitute one value for one other valuevi. Meanwhile, polyalphabetic ciphers can substitute one value for several. From Polybius’ description of the encoding square it would be another hundred years until we see what is widely credited as one of the first true substitution ciphers of the western world, the Caesar Cipher.
Credited to Julius Caesar around the mid 1st century CE. This simple substitution cipher replaces each letter with one three positions to the right, with the substitution value alphabet wrapping at the end. This is also known as a shift or rotational (ROT) cipher due to the shifting/rotational nature of the encrypting alphabet values.
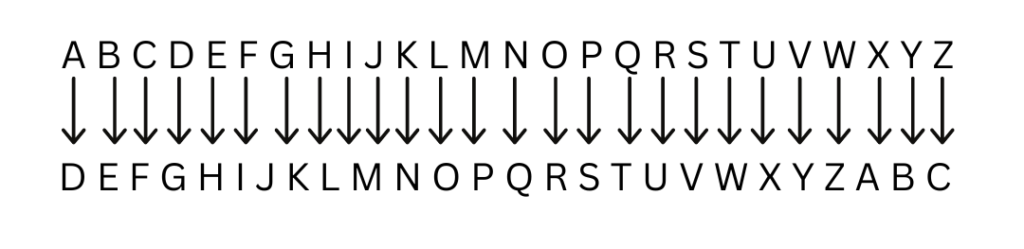
The actual number of shifts or rotations is arbitrary so long as that value is known to both the sender and the recipient. Using the example shown above we would encrypt the plaintext value of CAT as FDW. To decrypt the message you simply perform the inverse operation on the enciphered text.
Over the next several hundred years the use of the cryptographic systems we have discussed so far would spread north and west. To the north we see the Polybius coordinate system adopted to various runic alphabets. Across the rest of Europe substitution ciphers would evolve to make use of numbers and symbols but the same basic monoalphabetic substitution scheme was employed, to greater or lesser extent, throughoutvii. While the art and science of cryptography continued to spread it would not be until the mid 15th century that we would see the next major advancement in western cryptography, the polyalphabetic cipher.
Leon Battista Alberti documented what is believed to be the first polyalphabetic cipher approach around 1467. To create his cipher Alberti describes the use of one of the earliest known encipherment machines the cipher wheel (see header graphic) which he called the ‘formula’. The formula consisted of two wheels. The outer wheel, called the stablis because it remained in position, and an inner wheel, mobilis, which could be rotated as needed. There are several ways that this device can be used to encipher or decipher text. The principle method, as described by Alberti, is to arbitrarily change the position of the mobilis throughout the encipherment process and indicate the correct index positioning in the cipher text with a capital letter. For example, we might encode ‘cat and dog’ as ‘Rniw iqz Pmvb’viii. Here we would start by aligning the inner letter R with the predetermined outer letter, let’s say K. We then encrypt each character in the message text (outer wheel) with the corresponding cipher character (inner wheel). This continues until we reach the next capital letter, P, so we realign the mobilis so that now K aligns with P and then continue the operation until we reach another capital letter or the message ends. The result is a cipher text where a given source character can, and probably will, have multiple ciphertext output values. While there are many polyalphabetic systems that would be developed in period this would be one of the very first and it earned Alberti the moniker of being the ‘Father of Western Cryptography’ for its innovation.
From 1500 onward cryptography began to emerge as a critical communication science. In 1518 Johannes Trithemius would publish ‘Polygraphia’, the first western book dedicated to the topics of cryptography and steganography. Other luminaries would soon follow and the works of cryptographers such as Bellaso, Cardano, Porta, and Vigenère would continue to advance the art and science of cryptography throughout the 16th century. The tools, techniques, and principles that were pioneered during this time would create the foundation of what we know of as modern cryptography.
Johannes Trithemius, Polygraphia (1518), National Cryptologic Museum, Photo by Kevin Baun
For more information on period cryptography you can visit Melchior’s Cryptography website located at https://crypto.houseblueheron.com/
References
Bauer, C. (2019). Unsolved!: The history and mystery of the world’s greatest ciphers from Ancient Egypt to online secret societies. PRINCETON University PRES.
Kahn, D. (1996). The codebreakers: The story of secret writing. Scribner.
iSteganography is the science of hiding information covertly. The message itself isn’t scrambled or obfuscated but rather hidden in such a way that only those with knowledge of its whereabouts may access it. Steganography is closely related to cryptography but is outside the scope of this introduction.
ii When I say ‘generally held’ you may refer to almost any respectable text on the subject of this history of cryptography to include luminaries such as Khan (1996), Bauer (2019), and others.
iii The Aneas Disc is described as a single disc 3-6inches (10-15cm) in diameter. Around the edge of this disc were holes that correspond to the letters of the alphabet. In the central area of the disc you will find two additional holes, one in the center and one that is used as a key to point to the first letter of the sequence. A string is tied from the center hole through each letter in the given message. A ‘dowbleth’, sequence of two identical letters ‘transposed’ against itself, is indicated by marking the target letter and then passing the string through the center hole. To ‘decrypt’ the message, the recipient simply remove the string to reconstruct the message backwards.
iv Polybius describes the square in his Histories but attributes the core technique to Cleoxenus and Democleitus.
v As a quick reminder: the focus here is on Western Cryptography. Substitution ciphers such as Atbash were known to Hebrew scholars as early at 600 BCE but it took some time for those techniques to make their way west.
vi This touches on the notion of ciphers that are affine or not. While that concept is beyond the scope of this short introduction it is also worth mentioning for those that wish to dig deeper.
vii I’m not including nomenclature ciphers here because while they do exchange whole words and even phrases the basic idea of individual substitution is maintained
viii Note that this is intentional gibberish and is only provided as an example of how to know when and to where the mobilis should be adjusted.
